-
What is secure software development?
-
Why is secure software development important?
-
What is a secure software development lifecycle?
-
Secure software development lifecycle (S-SDLC) process
- What are the most common software security risks?
-
Top 10 software development security best practices
- 1. Implement secure coding practices
- 2. Conduct security awareness training
- 3. Identify potential security threats with code reviews
- 4. Penetration testing
- 5. Develop secure software using DevOps practices
- 6. Encrypting data and handling it securely
- 7. Develop your project using a secure framework
- 8. Incident response plan
- 9. Least privilege principle
- 10. Input validation and sanitization
-
Final words
-
How can OpenXcell help you with secure software development?
Since cyber-attacks have risen dramatically recently, secure software development is more important than ever.
Enterprise Strategy Group reports that organizations have been attacked due to misconfigurations, software vulnerabilities in proprietary and open-source code, and access issues. In most cases, these mistakes can be prevented if the right tools are in place to identify and resolve issues before cloud applications are deployed. The goal is not only to test or scan before deployment; it’s also to assist developers in quickly resolving running problems.
According to the research, most organizations (68%) prioritize developer-focused security products to transfer some responsibilities to developers. However, only 31% realize the importance of developer-focused security products. Only 1% of people didn’t prioritize security approaches that shift security left.
Implementing secure software development practices is crucial to counter these threats. Let’s delve into the key aspects of software development lifecycle security to fortify your software against evolving cyber threats.
What is secure software development?
Secure software development aims to reduce the risk of security vulnerabilities in software by designing, building, and testing it. It requires incorporating security considerations into the development life cycle, from the first design to the final deployment. Secure software engineering practices can assist developers in creating safer and more secure software applications. When an application is poorly developed, there is a high risk of attackers compromising information, resources, and damaging other aspects of the company. The best way to ensure security is to incorporate good protocols into the security architecture even before the requirements are formed.
Why is secure software development important?
According to projections, it is predicted that cybercrime will cost the global economy $10.5 trillion by 2025, an increase of 15% annually. There has never been a more vulnerable time for businesses, even those with substantial cybersecurity defenses.

There is a huge number of hackers on the internet who are looking for easy ways to compromise software applications through hacking, phishing, and ransomware attacks. Software’s security barriers are weakened by specific flaws that hackers exploit to compromise its functionality. Ultimately, this leads to the theft of confidential information, financial loss, and damage to a company’s reputation and brand.
Secure software development is the only way to prevent this from happening. There can be legal consequences and compliance issues associated with software defects and vulnerabilities, resulting in expensive fines and penalties.
What is a secure software development lifecycle?
The Secure Software Development Lifecycle, or SDLC, is a structured process that facilitates the development of high-quality software applications in the shortest amount of time at the lowest cost. Furthermore, a secure SDLC gathers security requirements alongside functional requirements, performs routine risk analysis during the design phase, and conducts security testing concurrently with development.
Secure software development lifecycle (S-SDLC) process
There are five essential phases in the Secure Software Development Lifecycle that a software development company cannot ignore. Let’s have a look!
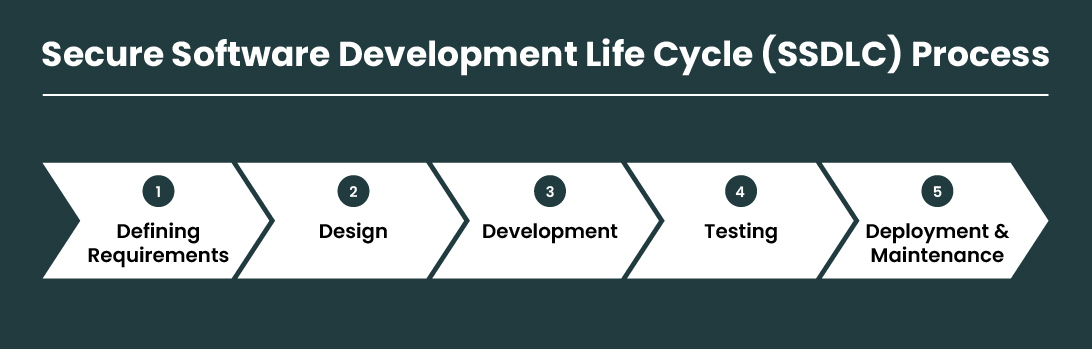
1. Defining requirements
Any project development requires proper planning. You have already achieved 80% foolproof development if you have a reliable plan. During this phase, you’ll need to identify your project’s security requirements. As a result, you gain an essential understanding of how you need to design security protections for the software you’re developing and which aspects of it need more consideration.
2. Design
As soon as the planning phase is complete, the design phase begins. The key point to remember here is that software design must reflect earlier planning and should be done based on the future deployment of the project. This phase involves implementing and coding security requirements according to secure coding standards. An organization’s security architecture should consider all relevant security requirements, control risk management and legal constraints, as well as implementing all relevant security requirements.
3. Development
Following that comes the actual software development, which is the actual coding and programming of the application. The developers must follow secure coding standards, implement secure design patterns and frameworks, and make use of the latest secure coding practices in the development.
4. Testing
After the design and development phases are complete, the product can be sent out for alpha and beta testing. This phase is usually underestimated by most companies, and they try to skip it, but they later regret their omission. Hire professional software testers to attempt to hack the software and pass the project through a series of rigorous security tests. Your project’s weak spots will be recorded by these testers and subsequently reported to you. You can also get suggestions on how to improve the security for software development.
5. Deployment and maintenance
After you have meticulously followed all the above steps, it is time to deploy your software. If you have followed all the above steps meticulously, your deployment will be a smooth one. However, deployment is just the beginning of a developer’s work. Applications must be updated regularly, and issues must be addressed as soon as they arise. Software maintenance and aftercare are equally important to a secure software development process.
What are the most common software security risks?
- A lack of active maintenance of software systems
- Coding errors
- Vulnerable web services
- Security of passwords
- Legacy software
It is essential to understand the most common security risks developers face before listing best practices. The following are some of the common security risks faced by software developers:
1. A lack of active maintenance of software systems
It is likely that your software applications have vulnerabilities if you are no longer developing them or using a small team to support them. The hackers would be able to access confidential and secure information stored on your server once these vulnerabilities are exploited.
2. Coding errors
Poorly written code is another common software development risk. Frequently, poorly written code makes it challenging to secure an application, and input validation, output encoding, error handling, secure storage, and secure coding practices are not followed. In order to build secure software without any coding errors, you should hire a skilled software engineer.
3. Vulnerable web services
Data related to the user and personal information is often stored in web services. Hackers may exploit vulnerabilities in your web services to gain access to sensitive information or perform unauthorized activities.
4. Security of passwords
Dictionary attacks and brute force attacks are two methods used by attackers to steal and decrypt passwords when passwords are not stored in a safer way. Passwords should be secured using strong cryptography.
5. Legacy software
Security attacks can happen with legacy software. Often, they are written without secure coding practices and aren’t updated frequently, which makes them vulnerable to cyber-attacks.
Top 10 software development security best practices
Vulnerabilities in software are very real threats. Here is a report from Qualys Web Application Scanner. According to the report, 370,000 web applications were scanned. Over 25 million vulnerabilities were found during the scans! Here are ten software security development best practices that can help you plug these vulnerabilities.

1. Implement secure coding practices
Secure coding practices are the best way to build secure software. It is important to follow established guidelines and standards for writing secure code, such as those provided by organizations such as OWASP (Open Web Application Security Project) and CERT (Computer Emergency Response Team). An attacker can exploit common vulnerabilities and weaknesses in software applications by following secure coding practices.
A secure coding practice involves validating input to prevent injection attacks, implementing secure authentication and access controls to prevent unauthorized access, and encrypting sensitive data. Furthermore, secure coding practices ensure that software components are updated with the latest security patches and use secure coding techniques to prevent buffer overflows.
2. Conduct security awareness training
You need to inform your software developers about the challenges they face. It is important to inform them about common attacks in the software development industry and how to avoid them. Security awareness training should cover common software development vulnerabilities. In addition, it should include information about how hackers and cybercriminals operate.
Developing software requires developers to know what mistakes they are likely to make when writing code in order to avoid making the same mistakes. Your software developers will be able to write secure applications from the start with education and knowledge transfer.
During security awareness training, it’s a good idea to hold regular meetings where everyone can discuss secure development practices. Having these meetings can be very helpful when it comes to identifying vulnerabilities in your code before cyber-attackers do.
3. Identify potential security threats with code reviews
In order to avoid common pitfalls, code reviews help developers identify and fix security vulnerabilities. Software development requires secure design. Take a defensive stance when you are writing code to help you write as little code as possible. Additionally, you should test your code and write unit tests for all areas of concern.
Every time you make a code change, you should check if the change has introduced any new security vulnerabilities. The development process should also be reviewed for security requirements in order to ensure that secure coding practices are adhered to.
4. Penetration testing
A penetration test identifies potential security issues in software by automating the process. An experienced penetration testing team specializing in software security can perform proper penetration tests.
The experts use the same tools hackers do to check how secure your system is. Every month, companies should perform penetration testing on a subset of their systems or products. By doing so, you can be confident that existing vulnerabilities will be addressed and resolved before attackers find them.
The security testing process also involves identifying and mitigating vulnerabilities in third-party software components. Moreover, companies should ensure that their code and vendors’ and partners’ products are secure.
5. Develop secure software using DevOps practices
Once you have implemented these best practices, make sure you incorporate them into your DevOps processes. As a result, the entire software development team will have a better understanding of security requirements and can build more secure applications.
Therefore, your team will be able to identify security issues early on instead of waiting until it’s too late. Therefore, secure DevOps (or DevSecOps ) practices are crucial to reducing vulnerabilities and eliminating bugs in software development from start to finish.
Businesses can even establish a bug bounty program to reward users who report security flaws in their apps. Last but not least, you should regularly communicate progress updates in your company so everyone knows where all these new policies are coming from.
6. Encrypting data and handling it securely
It’s important to follow security testing best practices to make sure data handling and encryption are secure. A security test should be conducted at every phase of the secure software development lifecycle (SDLC) to identify vulnerabilities. The process of identifying potential security risks and mitigating them involves vulnerability assessments, penetration testing, and threat modeling.
In custom software development, secure programming practices should also be followed. In this case, you have to follow security-focused coding standards, like avoiding insecure coding practices, using secure programming languages, and doing code reviews to find and fix bugs. As part of secure programming practices, users and systems should be granted only the access rights they need to perform their tasks, such as the principle of least privilege.
7. Develop your project using a secure framework
Software development security best practices are essential for creating secure software products. One of the best practices is using a secure development framework, which gives you a structured approach to building secure software. It may also include security testing, vulnerability scanning, and penetration testing to help developers create secure software products.
Developers can reduce the risk of security vulnerabilities, prevent attacks, and protect sensitive data by using a secure development framework. Developing secure software requires secure coding practices as well. The best way to prevent vulnerabilities that can be exploited by attackers is to follow coding standards and use coding best practices.
Keeping up to date with the latest security threats and vulnerabilities is crucial for developers. Software developers can prevent costly security breaches by following these best practices to create secure products that comply with industry standards and regulations.
8. Incident response plan
There is always the possibility of a breach, regardless of how closely you adhere to software security best practices. Even if attackers breach your systems, you can prevent them from achieving their mission if you prepare. Prepare an incident response (IR) plan to detect and limit the damage caused by an attack.
A comprehensive incident response plan is essential to address any security incidents or breaches during deployment. It should specify how the incident will be identified, contained, and communicated with stakeholders, as well as how the system will be restored to normal operation as soon as possible. Security incidents can be minimized, and the application can be kept secure by establishing a well-defined incident response plan.
It is therefore imperative that organizations have a well-defined incident response plan in place in order to deal with security incidents. Security incidents can be identified, contained, and recovered from by identifying potential dangers.
9. Least privilege principle
As mentioned earlier, security software development requires adhering to the principle of least privilege. It emphasizes granting users and systems the minimum level of access needed to perform their duties. Limiting permissions makes security breaches less likely and minimizes the paths through which attackers can exploit vulnerabilities.
You should conduct a thorough analysis of your software’s user roles and responsibilities before implementing the least privilege principle. Also, ensure users only have access to the resources and functionalities they need for their roles by assigning permissions. Be sure to review and update access privileges on a regular basis, especially as roles change.
10. Input validation and sanitization
Your software needs to be robustly validated and sanitized in order to combat various cyber threats.
The first thing you can do is treat all user-supplied data as potentially harmful and implement stringent input validation procedures. Check inputs to make sure they’re the right type, length, and format. You should use server-side validation in addition to client-side validation to prevent malicious manipulation.
Lastly, emphasize the importance of input validation and sanitization during developer training sessions, fostering a proactive mindset toward secure coding practices. By diligently applying these practices, you establish a robust shield against a wide range of common security threats stemming from user inputs.
Final words
The implementation of security best practices during the secure software development lifecycle security is essential. Organizations can enhance security for software development and mitigate risks by implementing the ten practices outlined in this article.
The development process can be strengthened by prioritizing security from the start and integrating it throughout. It involves doing risk assessments, defining security requirements, and using secure coding practices. Vulnerabilities can be identified early with regular security testing.
Fostering a security-conscious culture requires clear security policies, guidelines, and training programs. Software security also requires regular updates, patch management, and careful evaluation of third-party components.
How can OpenXcell help you with secure software development?
When you choose OpenXcell for your software development needs, you can rest assured that we are committed to a secure software development process. Our seasoned team excels at integrating cutting-edge security measures into your applications.
We bring a holistic approach to secure software development, encompassing stringent code reviews, robust input validation, and the implementation of the least privilege principle. As a leading software development company, we prioritize staying ahead of the security curve, employing state-of-the-art encryption, comprehensive access controls, and continuous monitoring to create a robust defense against emerging cyber threats.
By selecting OpenXcell as your development partner, you are opting for a team that recognizes the paramount importance of security in today’s digital landscape. Let’s connect!








